8.5 – Securing E-Mail
- Pretty Good Privacy (PGP) provides secure e-mail. Requiring only client and server application code, PGP was one of the first security technologies to be broadly used in the Internet.
8.5.1 – Secure E-Mail
- Important security features is:
- Confidentiality
- Sender authentication
- Message integrity
- Receiver authentication
- Confidentiality:
- The most straightforward way to provide this is to encrypt the message with symmetric key technology. If the symmetric key is long enough, and if only the receiver and sender has the key, then it is extremely difficult for anyone else to read the message.
- This can be fundamentally difficult which is why we naturally consider an alternative approach.
- Public key cryptography (f.ex. RSA) is a good alternative assuming that Alice knows for sure that the public key is Bob’s public key, this approach is an excellent means to provide the desired confidentiality.
- One problem, is that public key encryption is relatively inefficient, particularly for long messages.
- To overcome the efficiency problem, let’s make use of a session key. In particular:
- Alice selects a random symmetric session key, ,
- Encrypts her message, m, with the symmetric key
- Encrypts the symmetric key with Bob’s public key,
- Concatenates the encrypted message and the encrypted symmetric key to form a “package”
- Sends the package to Bob’s e-mail address
- When bob receives the package he:
- Uses his private key, to obtain the symmetric key,
- Uses the symmetric key to decrypt the message m
- The most straightforward way to provide this is to encrypt the message with symmetric key technology. If the symmetric key is long enough, and if only the receiver and sender has the key, then it is extremely difficult for anyone else to read the message.
- Authentication and message integrity:
- Suppose for the moment that Alice and Bob are no longer concerned with confidentiality, and are concerned only about sender authentication and message integrity.
- To accomplish this we use digital signature and message digests:
- Alice applies a hash function, H, to her message, m, to obtain a message digest.
- Alice signs the result of the has function with her private key, , to create a digital signature.
- Alice concatenates the original message with the signature to create a package.
- Alice sends the package to Bob’s e-mail address.
- When Bob receives the package, he:
- Bob applies Alice’s public key, to the signed message digest
- Bob compares the result of this operation with his own hash, H, of the message.
- Designing an e-mail system that provides confidentiality, sender authentication, and message integrity:
- Alice first creates a preliminary package, that consists of her original message along with a digitally signed hash of the message. As the steps in the first image bellow.
- Alice treats this preliminary package as a message in itself and sends this new message through the sender steps, creating a new package that is sent to Bob. As the steps in the third image bellow.
- When Bob receives the package, he first applies his side of the second image bellow and then his side of the first image bellow.
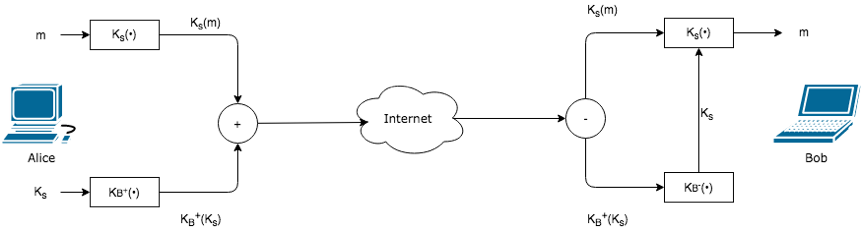
Figur 1 Alice used a symmetric session key, , to send a secret e-mail to Bob
Figur 2 Using hash functions and digital signatures to provide sender authentication and message integrity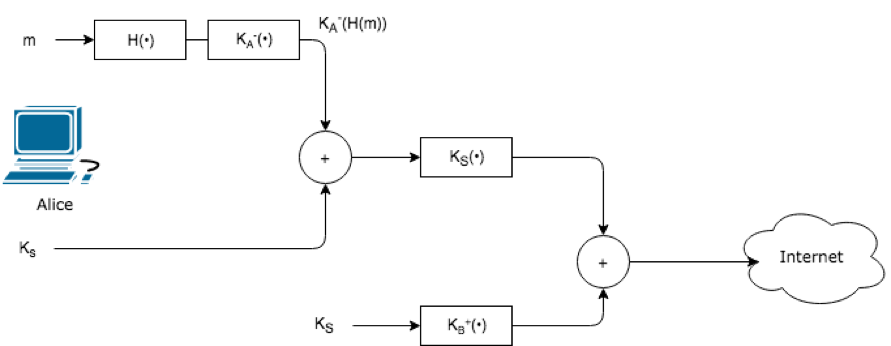
Figur 3 Alice uses symmetric key cryptography, public key cryptography, a has function, and a digital signature to provide secrecy, sender authentication, and message integrity
- The secure e-mail system design in the image above probably provides satisfactory security for most e-mail users for most occasions. But there is still one important issue:
- It requires Alice to obtain Bob’s public key, and requires Bob to obtain Alice’s public key.
- The distribution of these public keys is a nontrivial problem.
- An intruder might masquerade as Bob and give Alice h*r own public key while saying that it is Bob’s public key, enabling her to receive the message meant for Bob.
- A popular approach is to securely distribute public keys is to certify the public keys using a CA.