7.3 – WiFi: 802.11 Wireless LANs
- The most popular wireless LAN technology is IEEE 802.11 wireless LAN (WiFi)
- All 802.11 standards share some common characteristics:
- They all use the same medium access protocol, CSMA/CA.
- They use the same frame structure for their link-layer frames.
- They have the ability to reduce their transmission rate in order to reach out over greater distances.
- 802.11 products are also all backwards compatible.
- The 2.4 GHz is an unlicensed frequency band, where 802.11 devices may compete for frequency spectrum with other devices.
- At 5 Ghz, it have a shorter transmission distance for given power level and suffer more from multipath propagation.
- Standard Frequency Range Data Rate
- 802.11b 2.4 GHz Up to 11 Mbps
- 802.11a 5 GHz Up to 54 Mbps
- 802.11g 2.4 GHz Up to 54 Mbps
- 802.11n 2.5 and 5 GHz Up to 450 Mbps
- 802.11ac 5 GHz Up to 1300 Mbps
- 802.11n and 802.11ac uses multiple input multiple-output (MIMO) antennas.
- 802.11ac base stations may transmit to multiple stations simultaneously, and use “smart” antennas to adaptively beamform to target transmissions in the direction of a receiver. Which decreases interference and increases the distance reached.
7.3.1 – The 802.11 Architecture
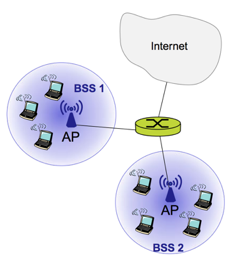
- The fundamental building block of the 802.11 architecture is the basic service set (BSS).
- A BSS contains one or more wireless stations and a central base station, known as an access point (AP) in 802.11 parlance.
- Interconnection device = f.ex. switch or router
- In a typical home network, there is one AP and one router (typically integrated together as one unit) that connects the BSS to the internet.
- Each 802.11 wireless station has a 6-byte MAC address.
- Each AP also has a MAC address for its wireless interface.
- Wireless LANs that deploy APs are often referred to as infrastructure wireless LANs, but IEEE 802.11 stations can also group themselves together to form an ad hoc network.
- In 802.11, each wireless station needs to associate with an AP before it can send or receive network-layer data.
- AP’s has a Service Set Identifier (SSID) that the admin choose, the admin must also choose a channel number:
- Recall that 802.11 operates in the frequency range of 2.4GHz to 2.4835 GHz. Within this 85 MHz band, 802.11 defines 11 partially overlapping channels.
- Any two channels are non. overlapping if and only if they are separated by four or more channels.
- The set of 1, 6, and 11 is the only set of three non-overlapping channels.
- F.ex. the admin could create a wireless LAN with an aggregate maximum transmission rate of 33 Mbps by installing 3 802.11b Aps at the same physical location, assigning channels 1, 6, and 11 to the APs, and interconnecting each of the APs with a switch.
- A WiFi jungle is any physical location where a wireless station receives a sufficiently strong signal from two or more APs (where each AP likely would be located on a different IP subnet and assigned to an independently channel).
- Suppose there are 5 APs in the WiFi jungle. To gain Internet access, your wireless device needs to join exactly one of the subnets and hence needs to associate with exactly one of the APs.
- Associate means the wireless device creates a virtual wire between them.
- Only the associated AP will send data frames to your wireless device, and your wireless device will send data frames into the Internet only through the associated AP.
- The 802.11 standard requires that an AP periodically send bacon frames, each of which includes the AP’s SSID and MAC address.
- A wireless device will search for bacon frames and choose one AP to associate with.
- The 802.11 Standard does not specify an algorithm for selecting which of the available APs to associate with, the algorithm is left up to the designers of the 802.11 firmware and software in your wireless device.
- Typically, the device chooses the AP whose bacon frame is received with the highest signal strength.
- A number of alternative ways of choosing APs has been proposed because an AP with the highest signal strength isn’t necessarily better than one with weaker strength and lower load compared to the one with highest strength, but more overloaded.
- The process of scanning channels and listening for beacon frames is known as passive scanning.
- Active scanning is the process of broadcasting a probe frame that will be received by all APs within the wireless device’s range. APs respond to the probe request frame with a probe response frame. The wireless device can then choose the AP with which to associate from among the responding APs.
- After selecting the AP to associate with, the wireless device sends an association request frame to the AP, and the AP responds with an association response frame.
- Note that this second request/response handshake is needed with active scanning, since an AP responding to the initial probe request frame doesn’t know which of the responding APs the device will choose from among multiple DHCP servers.
- After associating with the AP, the device will normally send a DHCP discovery message into the subnet via the AP to get an IP address.
- In order to create an association with a particular AP, the wireless device may be required to authenticate itself to the AP.
- One approach is to permit access to a wireless network based on a device’s MAC address.
- A second approach is to employ usernames and passwords.
- In both cases the AP typically communicates with an authentication server, relaying information between the wireless device and the authentication server using a protocol such as RADIUS.
7.3.2 – The 802.11 MAC Protocol
- We’ll refer to devices or the AP as wireless “stations” that share the multiple access channel.
- There’s three classes of multiple access protocols:
- Channel partitioning
- Random access
- Taking turns
- The designers of 802.11 chose a random access protocol referred to as CSMA with collision avoidance (CSMA/CA).
- Instead of using collision detection, 802.11 uses collision-avoidance techniques.
- Because of the relatively high bit error rates of wireless channels, 802.11 uses a link-layer acknowledgment/retransmission (ARQ) scheme.
- The 802.11 MAC protocol does not implement collision detection. There’s two reasons:
- The ability to detect collisions requires the ability to send and receive at the same time. Because the strength of the received signal is typically very small compared to the strength of the transmitted signal at the 802.11 adapter, it is costly to build hardware that can detect a collision.
- Even if the adapter could transmit and listen at the same time, the adapter would still not be able to detect all collisions, due to the hidden terminal problem and fading.
- Once a station begins to transmit a frame, it transmits the frame in its entirety; that is, once a station gets started, there is no turning back.
- 802.11’s link-layer acknowledgment scheme:
- When a station in a wireless LAN sends a frame, the frame may not reach the destination intact for a variety of reasons. To deal with this non-negligible chance of failure, the 802.11 MAC protocol uses link-layer acknowledgments.
- When the destination station receives a frame that passes the CRC, it waits a short period of time known as the Short Inter-frame Spacing (SIFS) and then sends back an acknowledgment frame.
- If the transmitting station des not receive an acknowledgment within a given amount of time, it assumes that an error has occurred and retransmits the frame, using the CSMA/CA protocol.
- If an acknowledgment is not received after some fixed number of retransmission, the transmitting station gives up and discards the frame.
- CSMA/CA protocol description:
- If initially the station senses the channel idle, it transmits its frame after a short period of time known as the Distributed inter-frame space (DIFS)
- Otherwise, the station chooses a random backoff value using binary exponential backoff and counts down this value after DIFS when the channel is sensed idle. While the channel is sensed busy, the counter value remains frozen.
- When the counter reaches zero, the station transmits the entire frame and then waits for an acknowledgment.
- If an acknowledgment is received, the transmitting stations knows that its frame has been correctly received at the destination station. If the station has another frame to send, it beings the CSMA/CA protocol at step 2. If the acknowledgment isn’t received, the transmitting station reenters the backoff phase in step 2, with the random value chosen from a larger interval.
- CSMA/CA refrains from transmitting while counting down, even when it senses the channel is idle, but why does it do this?:
- Let’s consider a scenario in which two stations each have a data frame to transmit, but neither station transmits immediately because each senses that a third station is already transmitting.
- Because 802.11 does not detect a collision and abort transmission, a frame suffering collision will be transmitted in its entirety. The goal in 802.11 is this to avoid collisions whenever possible.
- In 802.11, if the two stations sense the channel busy, they both immediately enter random backoff, hopefully choosing different backoff values. If these values are indeed different, once the channel becomes idle, one of the two stations will begin transmitting before the other, and the “losing station” will hear the “winning statin’s” signal, freeze its counter, and regrain from transmitting until the winning station has completed its transmission.
- The 802.11 MAC protocol includes a nifty reservation scheme that helps avoid collisions even in the presence of hidden terminals.
- In order to avoid collision and wasted channel time caused by fading the IEEE 802.11 protocols allows a station to use a short Request to send (RTS) control frame and a short Clear to send (CTS) control frame to reserve access to the channel.
- When a sender wants to send a DATA frame, it can first send an RTS frame to the AP, indicating the total time required to transmit the DATA frame and the acknowledgment (ACK) frame.
- When the AP receives the RTS frame, it responds by broadcasting a CTS frame. This CTS frame serves two purposes:
- It gives the sender explicit permission to send and also instructs the other stations not to send for the reserved duration.
- The use of RTS and CTS frames can improve performance in two important ways:
- The hidden station problem is mitigated, since a long DATA frame is transmitted only after the channel has been reserved.
- Because the RTS and CTS frames are short, a collision involving an RTS and CTS frame will only last for the duration of the short RTS and CTS frame. Once the RTS and CTS frames are correctly transmitted, the following DATA and ACK frames should be transmitted without collision.
- Because RTS/CTS introduces delay and consumes channel resources it is only used to reserve the channel for the transmission of a long DATA frame.
- For many wireless stations, the default RTS threshold value is larger than the maximum frame length, so the RTS/CTS sequence is skipped for all DATA frames sent.
- If two nodes each have a directional antenna, they can point their directional antennas at each other and run the 802.11 protocol over what is essentially a point-to-point link.
7.3.3 – The IEEE 802.11 Frame

- Address 1 = MAC address of destination – wireless host or AP
- Address 2 = MAC address of source - wireless host or AP
- Address 3 = MAC address of router interface to which AP is attached
- The numbers above the first row is bytes and the numbers above the second row is in bits.
- Payload and CRC Fields:
- Typically consists of an IP diagram or an ARP packet. Although the field is permitted to be as long as 2312 bytes, it is typically fewer than 1500 bytes, holding an IP datagram or an ARP packet.
- The frame has a 32-bit cyclic redundancy check (CRC) so that the receiver can detect bit errors in the received frame.
- Address fields:
- The 802.11 frame has 4 address fields because it turns out that 3 address fields are needed for internetworking purposes (specifically for moving the network-layer datagram from a wireless station through an AP to a router interface)
- The fourth address field is used when APs forward frames to each other in ad hoc mode.
- Address 1 is the mac address of the wireless station that is to receive the frame. Thus if a mobile wireless station transmits the frame, address 1 contains the MAC address of the destination AP. Similarly, if an AP transmits the frame, address 1 contains the MAC address of the destination wireless station.
- Address 2 is the MAC address of the station that transmits the frame. Thus, if a wireless station transmits the frame, the station’s MAC address is inserted in the address 2 field. Similarly, if an AP transmits the frame, the AP’s MAC address is inserted in the address 2 field.
- Address 3, recall that the BSS (consisting of the AP and wireless stations) is part of a subnet, and that this subnet connects to other subnets via some router interface. Address 3 contains the MAC address of this router interface.
- Suppose there are two APs each of which is responsible for a number of wireless stations. Each of the APs has a direct connection to a router, which in turn connects to the global internet. We should keep in mind that an AP is a link-layer device, an thus neither “speaks” IP nor understands IP addresses. Consider now moving a datagram form the router interface R1 to the wireless station H1. The router is not aware that there is an AP between it and H1; from the router’s perspective, H1 is just a host in one of the subnets to which it (the router) is connected.
- The router, which knows the IP address of H1, uses ARP to determine the MAC address of H1, just as in an ordinary Ethernet LAN. After obtaining H1’s MAC address, router interface R1 encapsulates the datagram within an Ethernet frame. The source address field of this frame contains R1’s MAC address, and the destination address field contains H1’s MAC address.
- When the Ethernet frame arrives at the AP, the AP converts the 802.3 Ethernet frame to an 802.11 frame before transmitting the frame into the wireless channel. The AP fills in address 1 and address 2 with H1’s MAC address and its own MAC address, respectively, ad described above. For address 3, the AP inserts the MAC address of R1. In this manner, H1 can determine the MAC address of the router interface that sent the datagram into the subnet.
- Now consider what happens when the wireless station H1 responds by moving a datagram from H1 to R1:
- H1 creates an 802.11 frame, filling the fields for address 1 and address 2 with the AP’s MAC address and H1’s MAC address. For address 3, H1 inserts R1’s MAC address.
- When the AP receives the 802.11 frame, it converts the frame to an Ethernet frame. The source address field for this frame is H1’s MAC address, and the destination address field is R1’s MAC address. Thus, address 3 allows the AP to determine the appropriate destination MAC address when constructing the Ethernet frame.
- Sequence number, Duration, and Frame Control Fields:
- Because acknowledgments can get lost, the sending station may send multiple copies of a given frame. The use of sequence numbers allows the receiver to distinguish between a newly transmitted frame and the retransmission of a previous frame.
- The sequence number field thus serves exactly the same purpose here at the link layer as it did in the transport layer.
- The duration field is used for the time period that the sender wants to reserve the channel to transmit its data frame and and receive acknowledgment frame.
- The frame control field includes many subfields.
- The type and subtype fields are used to distinguish the association, RTS, CTS, ACK, and data frames.
- The to and from fields are used to define the meanings of the different address fields (these meanings change depending on whether ad hoc or infrastructure modes are used and, in the case of infrastructure mode, whether a wireless station or an AP is sending the frame).
- The WEP fied indicates whether encryption is being used or not.
7.3.4 – Mobility in the same IP Subnet
- In order to increase the physical range of a wireless LAN, companies and universities will often deploy multiple BSSs within the same IP subnet.
- Example of mobility between BSSs in the same subnet:
- Let’s consider two interconnected BSSs with a host, H1, moving from BSS1 to BSS2.
- Because in this example the interconnected device that connects the two BSSs is not a router, all of the stations in the two BSSs, including the APs, belong to the same IP subnet.
- When H1 moves from BSS1 to BSS2, it may keep its IP to the same IP address and all of its ongoing TCP connections. If the interconnection device were a router, then H1 would have to obtain a new IP address in the subnet in which it was moving.
- This address change would disrupt any on-going TCP connections to H1.
- As H1 wanders away from AP1, H1 detects a weakening signal form AP1 and starts to scan for a stronger signal. H1 receives beacon frames from AP2. H1 then disassociates with AP1 and associates with AP2, while keeping its IP address and maintaining its ongoing TCP sessions.
- How does the switch know that the host has moved from one AP to another?
- As you recall, switches are “self-learning” and automatically build their forwarding tables. This nicely handles occasional moves; however, switches were not designed to support highly mobile users who want to maintain TCP connections while moving between BSSs.
- Also recall that before the move, the switch has an entry in its forwarding table that pairs H1’s MAC address with the outgoing switch interface through which H1 can be reached. If H1 is initially in BSS1, then a datagram destined to H1 will be directed to H1 via AP1.
- Once H1 associates with BSS2, however, its frame should be directed to AP2.
- One solution is for AP2 to send a broadcast Ethernet frame with H1’s source address to the switch just after the new association. When the switch receives the frame, it updates its forwarding table, allowing H1 to be reached via AP2.
- The 802.11 1f standards group is developing an inter-AP protocol to handle these and related issues.
7.3.5 – Advanced Features in 802.11
- 802.11 Rate adaptation:
- Suppose a mobile 802.11 user who is initially 20 meters away from the base station, with a high signal-to-noise ratio. Given the high SNR, the user can communicate with the base station using a physical-layer modulation technique that provides high transmission rates while maintaining a low BER.
- Suppose the same user walk away from the base station, with the SNR falling as the distance from the base station increases. In this case, if the modulation technique used in the 802.11 protocol operating between the base station and the user does not change, the BER will become unacceptably high as the SNR decreases, and eventually no transmitted frames will be received correctly.
- 802.11 implementations have a rate adaption capability that adaptively selects the underlying physical-layer modulation technique to use based on current or recent channel characteristics.
- If a node sends two frames in a row without receiving an acknowledgment, the transmission rate falls back to the next lower rate. If 10 frames in a row are acknowledged, or if a time that tracks the time since the last fallback expires, the transmission rate increases to the next higher rate. This rate adaptation mechanism shares the same “probing” philosophy as TCP’s congestion-control.
- When conditions are good, the transmission rate is increased until something “bad” happens; when something bad happens, the transmission rate is reduced.
- Power Management:
- The 802.11 standard provides power-management capabilities that allow 802.11 nodes to minimize the amount of time that their sense, transmit, and receive functions and other circuitry need to be “on”.
- The 802.11 power management operates as follows:
- A node is able to explicitly alternate between sleep and wake state. A node indicates to the access point that it will be going to sleep by setting the power-management bit in the header of an 802.11 frame to 1.
- A timer in the node is then set to wake up the node just before the AP is scheduled to send its beacon frame. Since the AP knows from the set power-transmission bit that the node is going to sleep, it knows that it should not send any frames to that node, and will buffer any frames destined for the sleeping host for later transmission.
- A node will wake up just before the AP sends a beacon frame, and quickly enter the fully active state. The beacon frames sent out by the AP contains a list of nodes whose frames have been buffered at the AP. If There are no buffered frames for the node, it can go back to sleep. Otherwise, the node can explicitly request that the buffered frames be sent by sending a polling message to the AP. With an interbeacon time of 100msec, a wakeup time of 260 msec, and a similarly small time to receive a beacon frame and check to ensure that there are no buffered frames, a node that has no frames to send or receive can be asleep 99% of the time.

